The computing continuum encompasses various resources, from the cloud to geographically distributed fog nodes and end devices. Applications running on the end devices can offload computing tasks to the fog nodes, whereby the response times are usually lower compared to outsourcing to the central cloud. This is very important for applications that require low latency.
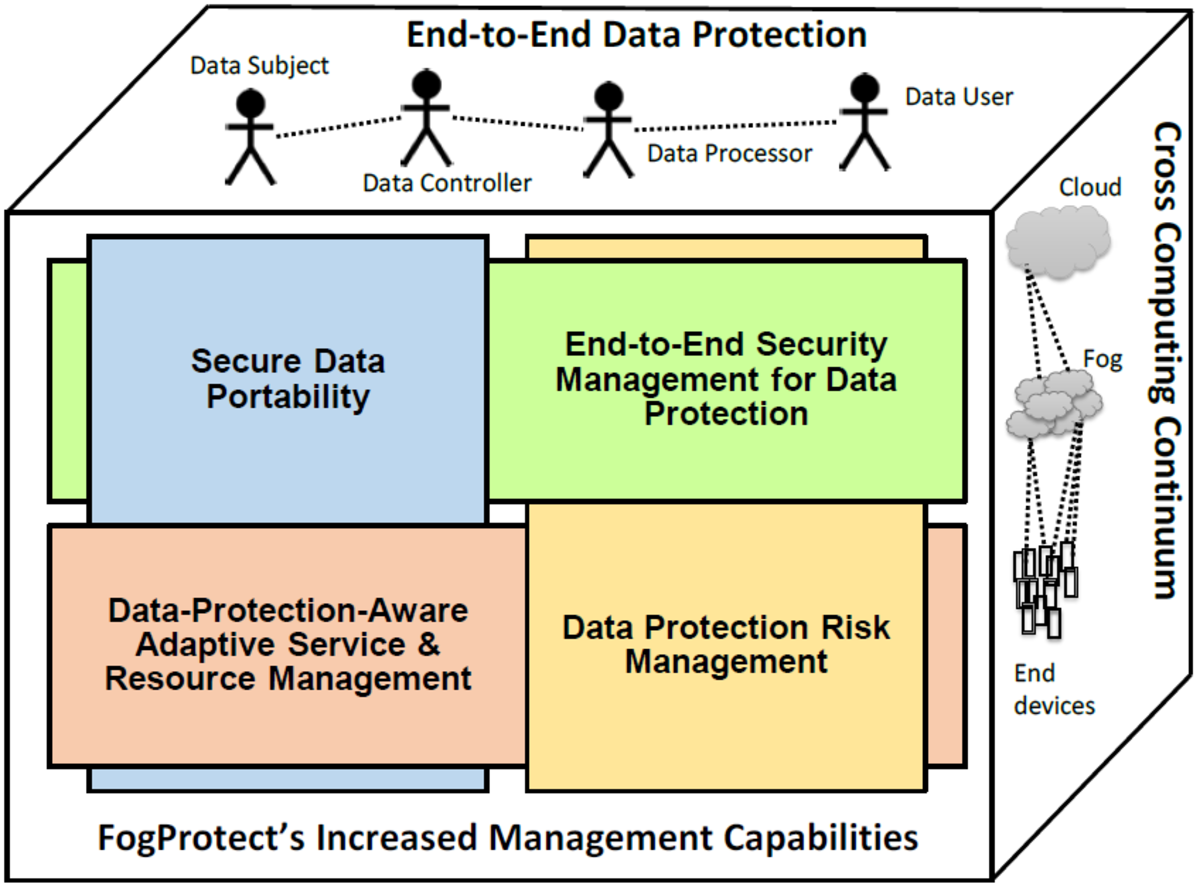
However, the execution of computational tasks or the storage of content in the computing continuum carries risks in terms of data protection. For example, malicious attackers have various options for gaining access to sensitive information. The goal of FogProtect is to ensure data protection in the computing continuum. To this end, new architectures, technologies and methods are being developed. The resulting solutions can be applied to various applications and services. The central focus of the project is on:
- secure data container technology for data portability and mobility
- data-protection-aware adaptive service and resource management
- advanced data protection policy management
- dynamic data protection risk management models and tools.
FogProtect provides generic technologies, mechanisms and solutions to ensure end-to-end data protection across the entire continuum, from cloud data centers to fog nodes and end devices. End-to-end data protection also includes the protection of data throughout the entire life cycle, taking into account the rights and obligations of the data subjects, data controllers, data processors, and the users of the data. In particular, FogProtect makes it easier for data controllers to comply with the relevant data protection regulations (such as the EU General Data Protection Regulation) and for data subjects to exercise the rights laid down in the regulation.
The paluno team is responsible for the work packages "End-to-End Data Protection Framework and Methodology" and "Service Management & Adaptation". The first work package ensures the alignment and integration of the individual solution components of the project. In the second work package, adaptive techniques for service and resource management will be developed to ensure an optimal balance between data protection, performance and energy consumption. In the computing continuum, changes in the network can occur frequently, for example by adding or removing a device. For this reason, the techniques developed must be able to react automatically to changes at runtime.
Funding
Funded by: European Union (Eu)
Program: Horizon 2020
Type: Research and Innovation Action
Funding: 699.500 EUR (Total Funded Amount 4,9 Mil. EUR)
Duration: 01/2020 - 12/2022
Website
Contact Person
Partners
- UBIWHERE LDA PT
- ATHENS TECHNOLOGY CENTER ANONYMI BIOMICHANIKI EMPORIKI KAI TECHNIKI ETAIREIA EFARMOGON YPSILIS TECHNOLOGIAS
- IBM ISRAEL - SCIENCE AND TECHNOLOGY LTD
- UNIVERSITY OF SOUTHAMPTON
- NOKIA SOLUTIONS AND NETWORKS GMBH &CO KG
- THALES SIX GTS FRANCE SAS
- TECHNISCHE UNIVERSITAET WIEN
- UNIVERSITAET DUISBURG-ESSEN
- DE VLAAMSE RADIO EN TELEVISIEOMROEPORGANISATIE
![[Translate to Englisch:] EU-Flagge [Translate to Englisch:] EU-Flagge](/fileadmin/_processed_/d/c/csm_EU-flag_eacbf9e465.jpg)
This project has received funding from the European Union's Horizon 2020 research and innovation programme under grant agreement no. 871525

